NIS2 Compliant – From Analysis to 24/7 Operational Readiness
We strengthen cyber resilience and document compliance with the NIS2 Directive (EU 2022/2555) and EC Regulation 2024/2690. We provide audits, process/technology implementation, and a 24/7 SOC service to meet the requirements for risk management measures (Article 21) and incident reporting (Article 23).


Who is affected by NIS2?
Each company should conduct an individual analysis to determine whether it is subject to the provisions of NIS2. The Directive, in its annexes, indicates the sectors from which entities may be considered “essential and important” and, if other requirements are met, will be subject to NIS2. These are m.in:
energy, transport
health, food
water and wastewater, waste management
public administration, post office
chemicals, selected production industries
Digital infrastructure
Space sector
Courier services
Production
Scientific research
MSP/MSSP services
What needs to be implemented in accordance
with the requirements of NIS2?
Implementation and maintenance of the Security Policy and documentation in the area of risk management
Development and implementation of security policies (including procedures and operational instructions) aligned with market standards. ISO 27001, defining roles and responsibilities for areas related to information security, developing and regularly conducting risk analysis, and managing the risk mitigation process.
Developing and maintaining incident handling processes in accordance with the requirements and deadlines indicated in NIS2
Security incident and incident management processes and procedures. Depending on the needs and size of the organization, it may also include playbooks describing the processes of handling security events, and a SOC 24/7 service.
Procedures/Policies and Tests Business Continuity (BCP) and Disaster Recovery (DR)
Conducting BIA (Business Impact Analysis), determining the required RTOs/RPOs for key systems, BCP/DR test schedule, and BCP/DR test reports
Supply chain management
Cyclical assessment of service providers and verification of suppliers in terms of their compliance with contractual provisions and market standards of information security, and audits of key suppliers.
Secure development and maintenance of applications and IT environments
Development of effective SDLC (Secure Software Development Lifecycle) processes, taking into account static and dynamic code analysis and SCA (Software Composition Analysis) for software produced internally and externally, Attack Surface Management (ASM) scans, and vulnerability management throughout the IT environment.
Evaluation of the effectiveness of the implemented security measures
Periodic security audits, KPIs/KRIs for security management processes, management reviews, cybersecurity management strategy in the enterprise, monitoring the implementation of corrective actions, and mitigating identified risks.
Maintaining Cyber Hygiene and continuous improvement of competence and awareness among staff
Training program (including for management), in particular, initial and recurring training for the entire staff, verification of employees’ knowledge through internal phishing/deep fake actions
Cryptography Management
Cryptography policy, in particular procedures for permitted encryption mechanisms and cryptographic key management.
Asset security management
Human Resources Management Policies, Access and Asset Management Policies, Asset Registers.
Secure Login Accesses and Methods
Identification and implementation (where applicable) of multi-factor authentication mechanisms in systems and services (MFA), use of effective cryptographic means in data transfer, and, where applicable, use of IAM (Identity and Access Management)/PAM (Privileged Access Management) systems.
| NIS2 Requirement | Description of security measures and evidence |
|---|---|
| Implementation and maintenance of the Security Policy and documentation in the area of risk management | Development and implementation of security policies (including procedures and operational instructions) aligned with market standards. ISO 27001, defining roles and responsibilities for areas related to information security, developing and regularly conducting risk analysis, and managing the risk mitigation process. |
| Developing and maintaining incident handling processes in accordance with the requirements and deadlines indicated in NIS2 | Security incident and incident management processes and procedures. Depending on the needs and size of the organization, it may also include playbooks describing the processes of handling security events, and a SOC 24/7 service. |
| Procedures/Policies and Tests Business Continuity (BCP) and Disaster Recovery (DR) | Conducting BIA (Business Impact Analysis), determining the required RTOs/RPOs for key systems, BCP/DR test schedule, and BCP/DR test reports |
| Supply chain management | Cyclical assessment of service providers and verification of suppliers in terms of their compliance with contractual provisions and market standards of information security, and audits of key suppliers. |
| Secure development and maintenance of applications and IT environments | Development of effective SDLC (Secure Software Development Lifecycle) processes, taking into account static and dynamic code analysis and SCA (Software Composition Analysis) for software produced internally and externally, Attack Surface Management (ASM) scans, and vulnerability management throughout the IT environment. |
| Evaluation of the effectiveness of the implemented security measures | Periodic security audits, KPIs/KRIs for security management processes, management reviews, cybersecurity management strategy in the enterprise, monitoring the implementation of corrective actions, and mitigating identified risks. |
| Maintaining Cyber Hygiene and continuous improvement of competence and awareness among staff | Training program (including for management), in particular, initial and recurring training for the entire staff, verification of employees’ knowledge through internal phishing/deep fake actions |
| Cryptography Management | Cryptography policy, in particular procedures for permitted encryption mechanisms and cryptographic key management. |
| Asset security management | Human Resources Management Policies, Access and Asset Management Policies, Asset Registers. |
| Secure Login Accesses and Methods | Identification and implementation (where applicable) of multi-factor authentication mechanisms in systems and services (MFA), use of effective cryptographic means in data transfer, and, where applicable, use of IAM (Identity and Access Management)/PAM (Privileged Access Management) systems. |
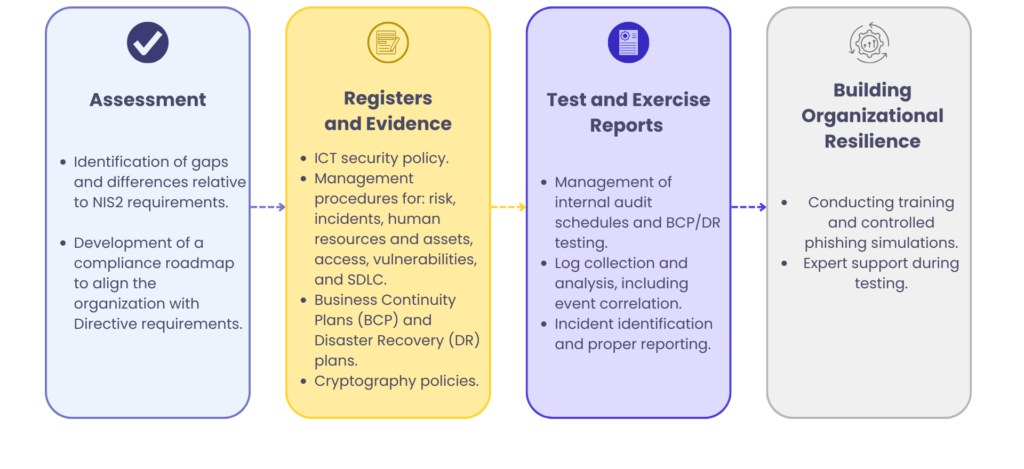
What do you receive as part of our
collaboration with Exorigo-Upos?
What are the deadlines for reporting incidents?
24 hA
warning to the CSIRTs/authorities.
72 h
pre-rated and IOC submission (if available).
1 month
final report; for ongoing incidents, a progress report, then a final one.

Why Exorigo-Upos?
End-to-end
From NIS2 vulnerability audit, through process/technology implementation, to 24/7 SOC and tests (pentests, tabletop). Our cyber services also include EDR implementation and maintenance, Email Security, vulnerability scanners, threat monitoring, consulting, and training.
ISO-compliant process
We verify processes against ISO/IEC 27001 and 22301 (compliance with Article 21).
Integrator experience
For years, we have delivered complex IT projects for retail chains and large enterprises across Europe. It provides practical background and experience in implementing systems and tools to improve ICT security.
Check which clients we work with: